A new Linux variant of a ransomware strain known as Play (also known as Balloonfly and PlayCrypt) that is targeted at VMware ESXi environments has been discovered by cybersecurity researchers.
In a report that was released on Friday, researchers from Trend Micro stated, “This development suggests that the group could be broadening its attacks across the Linux platform, leading to an expanded victim pool and more successful ransom negotiations.”
Play, which showed up on the scene in June 2022, is known for its double coercion strategies, encrypting systems in the wake of exfiltrating delicate information and requesting installment in return for an unscrambling key. . According to estimates released by Australia and the U.S., as many as 300 organizations have been victimized by the ransomware group as of October 2023.
According to Trend Micro’s data for the first seven months of 2024, the United States has the most victims, followed by Canada, Germany, the United Kingdom, and the Netherlands.
During that time, some of the most important industries that were impacted by the Play ransomware included real estate, professional services, construction, IT, retail, financial services, transportation, media, legal services, and manufacturing.
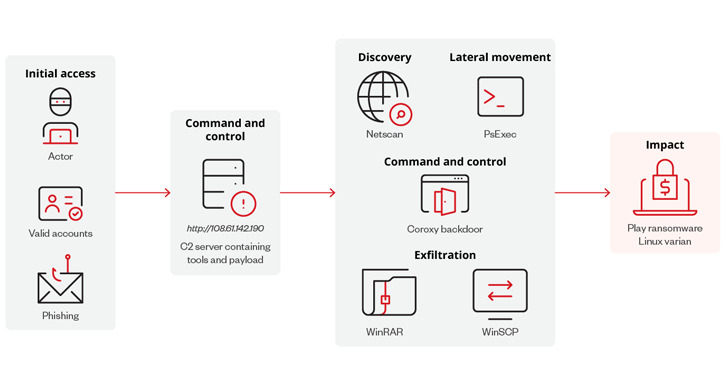
A RAR archive file hosted on an IP address (108.61.142[.]190) is the source of the cybersecurity firm’s analysis of a Linux version of Play. This file also contains other tools that have been identified as being used in previous attacks, such as PsExec, NetScan, WinSCP, WinRAR, and the Coroxy backdoor.
“The command-and-control (C&C) server hosts the common tools that Play ransomware currently uses in its attacks,” it stated, “Though no actual infection has been observed.” This could indicate that the Linux variant may utilize TTPs (similar tactics, techniques, and procedures).
The ransomware test, upon execution, guarantees that it’s running in an ESXi environment prior to continuing to encode virtual machine (VM) documents, including VM disk, configuration, and metadata records, and affixing them with the expansion “.PLAY.” The root directory is then emptied of a ransom note.
Further examination has confirmed that the Play ransomware group is possible utilizing the administrations and infrastructure peddled by Prolific Puma, which offers an illicit link shortening service to other cybercriminals to assist them with avoiding discovery while conveying malware.
In particular, it employs what’s known as an enlisted domain generation algorithm (RDGA) to turn up new domain names, an automatic mechanism that is progressively being utilized by a few threat actors, including VexTrio Viper and Revolver Rabbit for phishing, spam, and malware propagation.
Revolver Rabbit, for example, is accepted to have enlisted over 500,000 domains on the “.bond” Top level domain (TLD) at a surmised cost of more than $1 million, utilizing them as dynamic and decoy C2 servers for the XLoader (also known as FormBook) stealer malware.
In a recent analysis, Infoblox stated, “The most common RDGA pattern this actor uses is a series of one or more dictionary words followed by a five-digit number, with each word or number separated by a dash.” Instead of dictionary words, the actor sometimes uses ISO 3166-1 country codes, full country names, or numbers that correspond to years.”
RDGAs are significantly more challenging to detect and defend against than customary DGAs inferable from the way that they permit threat actors to create numerous domain names to enlist them for use – either at the same time or over the long haul – in their criminal foundation.
Infoblox stated, “In an RDGA, the threat actor registers all domain names and keeps the algorithm a secret.” In a customary DGA, the malware contains a calculation that can be found, and a large portion of the space names won’t be enrolled. DGAs are only used to connect to a malware controller, whereas RDGAs are used for many different types of malicious activity.”
The latest findings indicate a potential collaboration between two cybercriminal entities, suggesting that the Play ransomware actors are taking steps to bypass security protocols through Prolific Puma’s services.
Trend Micro came to the conclusion that “ESXi environments are high-value targets for ransomware attacks due to their critical role in business operations.” Because they are able to encrypt multiple virtual machines simultaneously and contain valuable data, they are more profitable for cybercriminals.”